How NotifyBreach Team Helped GitHub Prevent a Critical Security Breach
Published on 07 June 2025

Introduction
After a long hiatus, we are back with a new write-up. Although we don’t typically participate in bug bounty programs due to other commitments, we took up the challenge of hacking GitHub for a month and are excited to share our findings.
It all started when Shivam Singh (Mr. Rajput Hacker) reached out to me in November and encouraged me to try bug bounty. We decided to focus on npmjs.com, a subsidiary of GitHub. Despite the fact that GitHub is a large corporation and the bug bounty program was public on HackerOne, we felt that it was worth a shot.
Reconnaissance
In our pursuit of finding vulnerabilities in npmjs.com, Th3Pr0xyB0y (Vansh Devgan) and Mr Rajput Hacker (Shivam Singh) began by conducting a reconnaissance operation. We utilized our in-house product, X (part of the CyberXplore suite), to gather as much information as possible, including IP addresses, open ports, screenshots, and endpoints. With the power of cloud computing, the reconnaissance process was quick and efficient.
However, upon reviewing the information gathered, we found that there was limited scope for attack on the target, npmjs.com and npmjs.org. Our in-house product, X, made the reconnaissance process a breeze, and we’re excited to announce that the private beta will be available soon to the general public.
Focusing on Business Logic
Mr. Rajput Hacker and I decided to focus solely on business logic bugs in the application. Before we started our search, we made sure to understand the application completely. This involved minimal use of Burp Suite and a focus on understanding the core functionality and processes of the application.
Our goal was to find any weaknesses in the business logic that could potentially be exploited. By limiting our toolset and focusing on understanding the application, we aimed to uncover any unique or overlooked vulnerabilities. As npmjs.com was a relatively small application, our understanding and notes took us less than two hours to complete.
Vulnerabilities Discovered
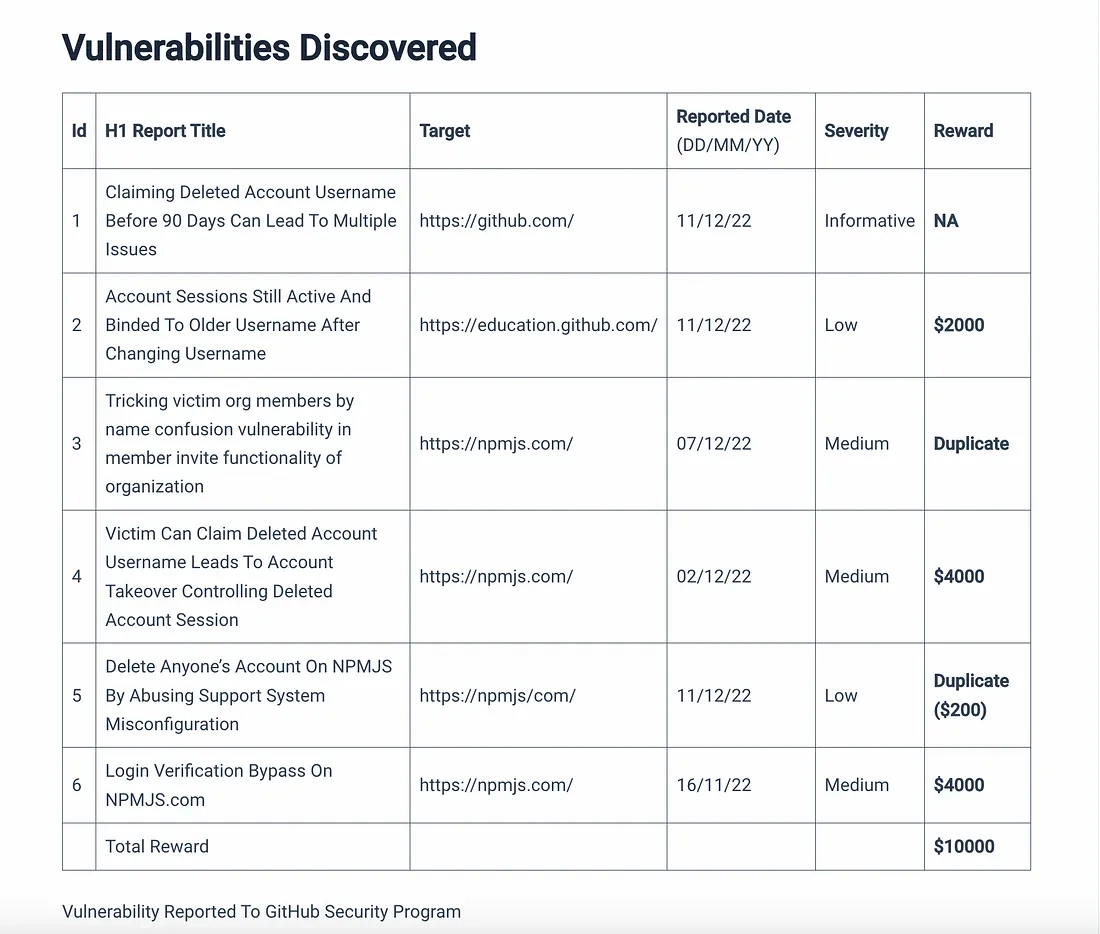
Even though we mentioned about 9 vulnerabilities being reported, we are going to write about 3 of them over here today which are given below:
- Login Verification Bypass On npmjs.com
- Pre-Account Takeover On npmjs.com
- Access Control Issue On education.github.com
Login Verification Bypass on npmjs.com
Description
While going through the authentication part of npmjs.com and common functionalities such as updating email address and profile update functionalities, we found out a weird behavior about an application that caught our eye which was the format of email verification link, password reset link & link sent to update the email address.
The link was formatted like https://npmjs.com/verify/{some_random_token_here} for all the functionalities—be it password reset, email verification link, or any XYZ link on this site for any purpose.
Next, we observed every time you log into the application, it sends a verification code to your registered email address and you have to enter that as part of the login verification feature (kind of 2FA/MFA code on email) to successfully log into the account. We then tried to bypass this functionality and were successful in doing so.
As we had completely explored the application in the last 2 hours, we knew each functionality well enough to relate and discover the bypass. Read the below steps to reproduce to see how we did it.
During our examination of the authentication process and common functionalities of npmjs.com, such as updating email addresses and profiles, we discovered a peculiar behavior in the format of email verification links, password reset links, and links sent to update email addresses. These links were formatted as https://npmjs.com/verify/{random_token}, and were used for all functionalities.
We also noticed that every time a user logged into the application, a verification code was sent to the registered email address. This verification code was required to complete the login process, acting as a form of two-factor authentication.
The second thing we noticed was that when updating an email address on npmjs, the update process would occur without requiring a password confirmation. An email would be sent to both the old and new email addresses. The email sent to the old address would inform the recipient that if the change was not made by them, they could click a link (https://npmjs.com/verify/{some_random_token_here}) to revert the change. The email sent to the new address would contain a link to verify the new email and link it to the account.
We encountered a surprising issue while trying to log into an account after updating the email address on the profile page. Despite not having confirmed or clicked on any links in either the old or the new email, the system displayed a message indicating that a verification code had been sent to the new, unverified address.
This seemed to suggest that we would not be able to log in. However, upon closer inspection, we discovered an email sent to our old address, asking us to revert the change to avoid account lockout. Upon clicking the provided link (https://npmjs.com/verify/{random_token}) to revert the email, we were directed to the login page. To our surprise, when we entered our credentials, the system did not ask for the verification code and instead allowed us to log in and revert the email change.
Our deep understanding of the application, gained from spending two hours familiarizing ourselves with its features, allowed us to relate different functionalities and find this bypass.
Read the Full Blog
Click Here To Read the Complete Blog Posted At CyberXplore Blog
Follow Our Security Researchers
- Twitter → @MrRajputHacker & @Th3Pr0xyB0y
- Instagram → @MrRajputHacker & @vanshdevgan
- LinkedIn → MrRajputHacker & @th3pr0xyb0y
- Medium → @mrrajputhacker & @th3pr0xyb0y


